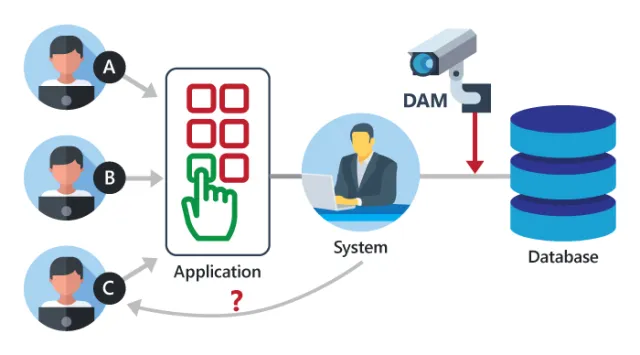
Database activity monitoring is done by combining several techniques such as network sniffing, memory scraping and reading system tables and database audit logs. Regardless of the methods used, DAM tools enable data correlation so as to provide an accurate picture of all the activities in the database.Database activity monitoring (DAM) refers to a suite of tools that can be used to support the ability to identify and report on fraudulent, illegal or other undesirable behavior, with minimal impact on user operations and productivity. The tools, which have evolved from basic analysis of user activity in and around relational database management systems (RDBMSs) to encompass a more comprehensive set of capabilities, such as discovery and classification, vulnerability management, application-level analysis, intrusion prevention, support for unstructured data security, identity and access management integration, and risk management support.
Our solution automatically discovers and classifies sensitive data from across the enterprise, providing real-time data activity monitoring and advanced user behavior analytics to help discover unusual activity around sensitive data.Deploy the solution to help discover regulated data in your data stores and use pre-built templates for regulations such as PCI, SOX, HIPAA, CCPA and many more, to streamline and automate compliance workflows.Our solution is built on a scalable architecture, which provides full visibility into structured, semi-structured and unstructured data activity across all major data repositories—stored on premises, in private and public cloud and in containers.Using a single interface, you can set access policies, monitor user access to protected data and discover, investigate and remediate vulnerabilities and threats as they occur in real time across your data environment.
While SSL decryption can drastically help improve security hygiene, organizations must be aware of the ramifications. Organizations often choose not to decrypt certain traffic, such as traffic containing medical or financial data, so they need to set up filters and policies help to ensure that these types of connections remain private.
Regardless, decrypting SSL traffic is an important aspect of an organization’s security, and most companies should be inspecting as much of their SSL traffic as they can, in order to reduce risk and keep their users and data safe.