Enterprise Security Solution
What’s the biggest challenge you face is Enterprise security to your business? How can you defend your organization from cyber attacks?
With innovative technology in security solutions and unmatched expertise, Winnovative’s IT Security solutions address all your security needs and protects your organization from cyber attacks.Enterprises require an integrated, AI based and collaborative security approach that automatically shares intelligence for real-time threat response. Winnovative will be able to provide Innovative IT Security solutions that meet your requirements.
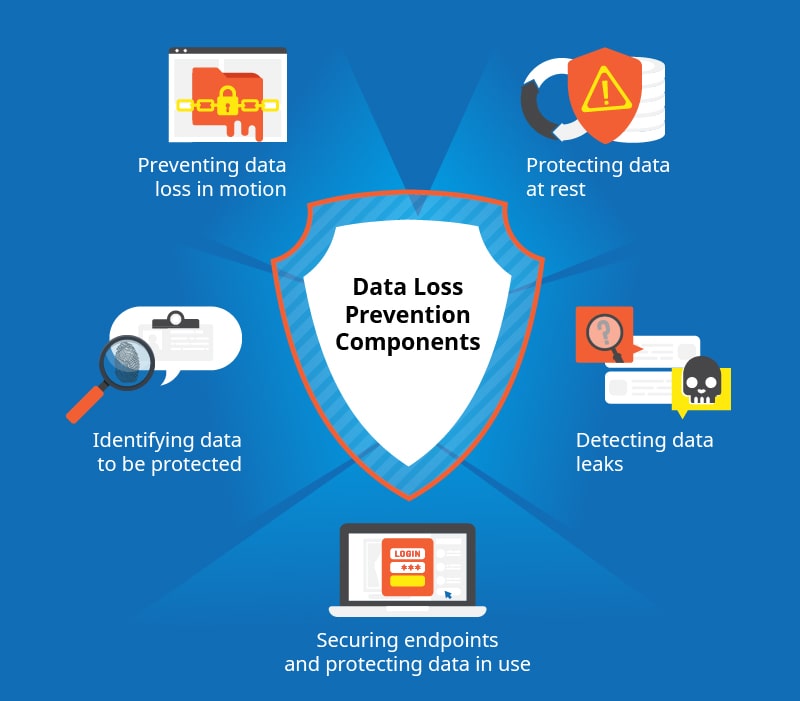
Data Leak Prevention
We see everything that happens to your organization’s sensitive data.Locate, understand, and protect your sensitive data
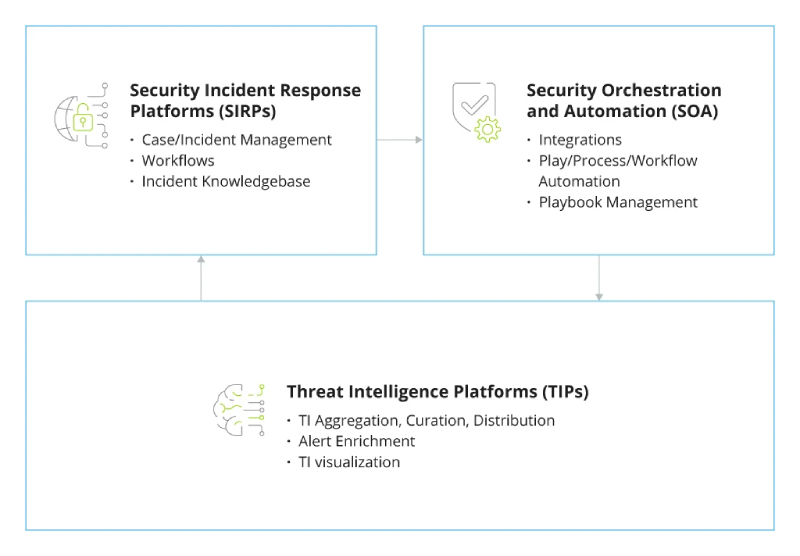
SIEM with orchestration
As SIEM software has transformed over time, the core components continue to provide value, while new, innovative technology — such as automation and new analytical techniques — has been built on top of the traditional SIEM foundation to provide the most comprehensive approach to reducing risk across an organization.This evolution of capabilities and features is often referred to as “next-gen SIEM.” The deployment of a next-gen SIEM solution delivers enhanced methods for securing data and solidifying operational excellence.
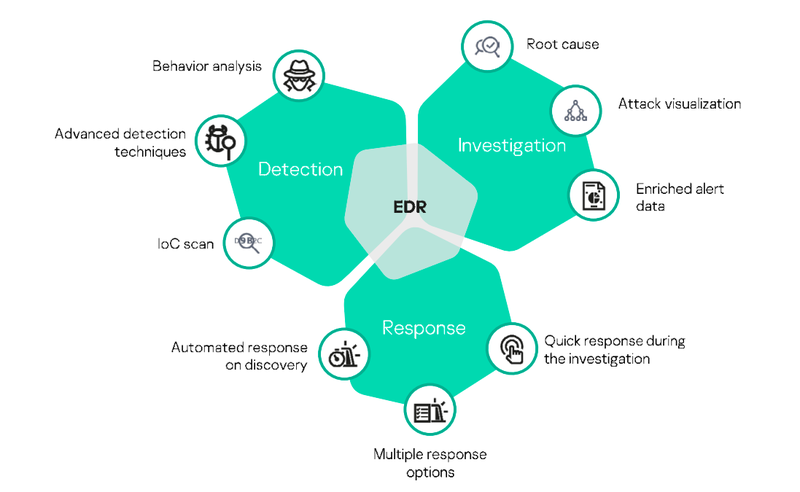
Endpoint Detection Response
Our EDR solution provides an innovative solution against threats in enterprises’ most critical and exposed assets, their endpoints! It creates dynamic & deceptive information which interferes with any attempt to recon the environment and deters the malware from executing its malicious intents, through all the stages of compromise in the Attack Kill Chain – covering advanced & sophisticated malware techniques, constantly making sure all the endpoints & data in the enterprise are secured.
Identity Security
As technology continues to bring more users, applications and data together, these connections also bring more vulnerability. Identity security is the easiest way to implement your digital transformation faster and reduce risk.Gain a complete view of all access across your organization, including those hidden or unknown that may pose inherent risk.Stay ahead of the security curve with AI enhanced visibility, detection and remediation that adapts as your organization evolves.
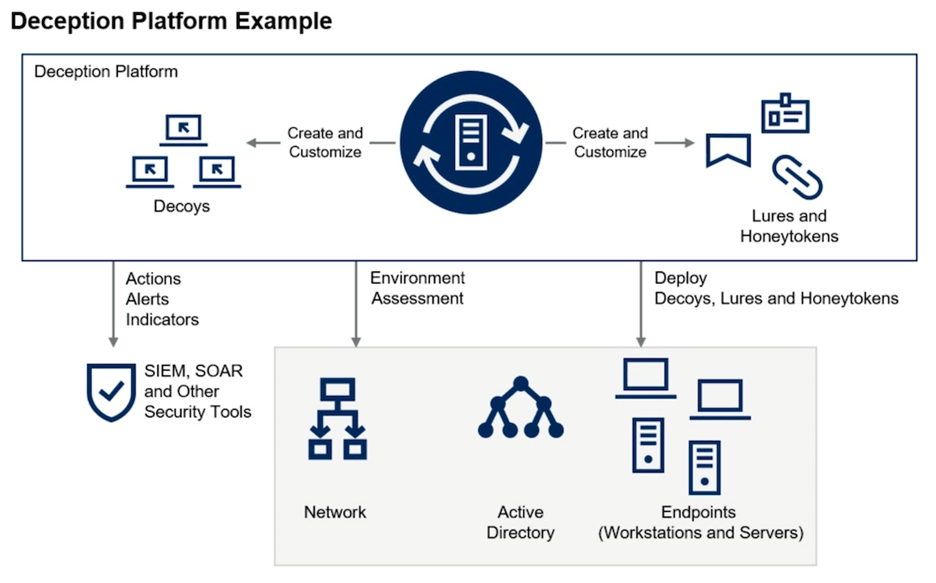
Network Deception
Our deception solution delivers unparalleled attack prevention, detection, and adversary intelligence collection based on cyber deception and data concealment technologies.
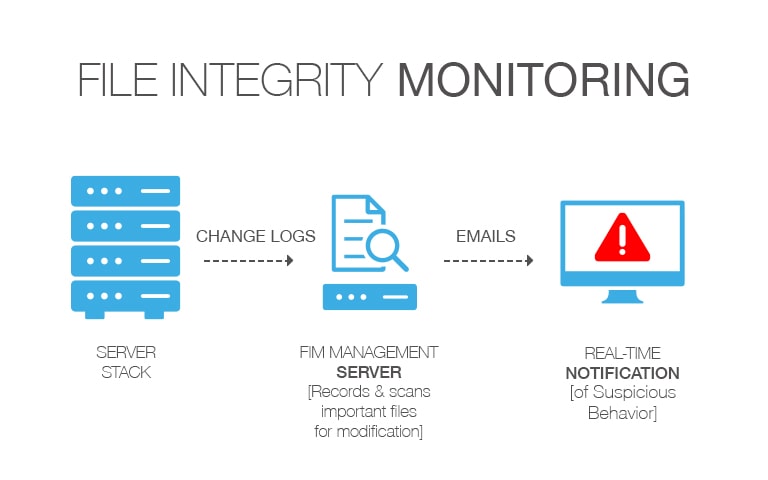
File Integrity Monitoring
File Integrity Monitoring solution provides critical and fundamental cyber security prevention and detection. It does this by leveraging the required security best practice disciplines of system configuration and integrity assurance combined with the most comprehensive and intelligent change control solution available.
Secure Config Review
Manage your network risks with our accurate firewall and network configuration audit tool. It discovers vulnerabilities in firewalls, switches and routers, automatically prioritizing risks to your organization.
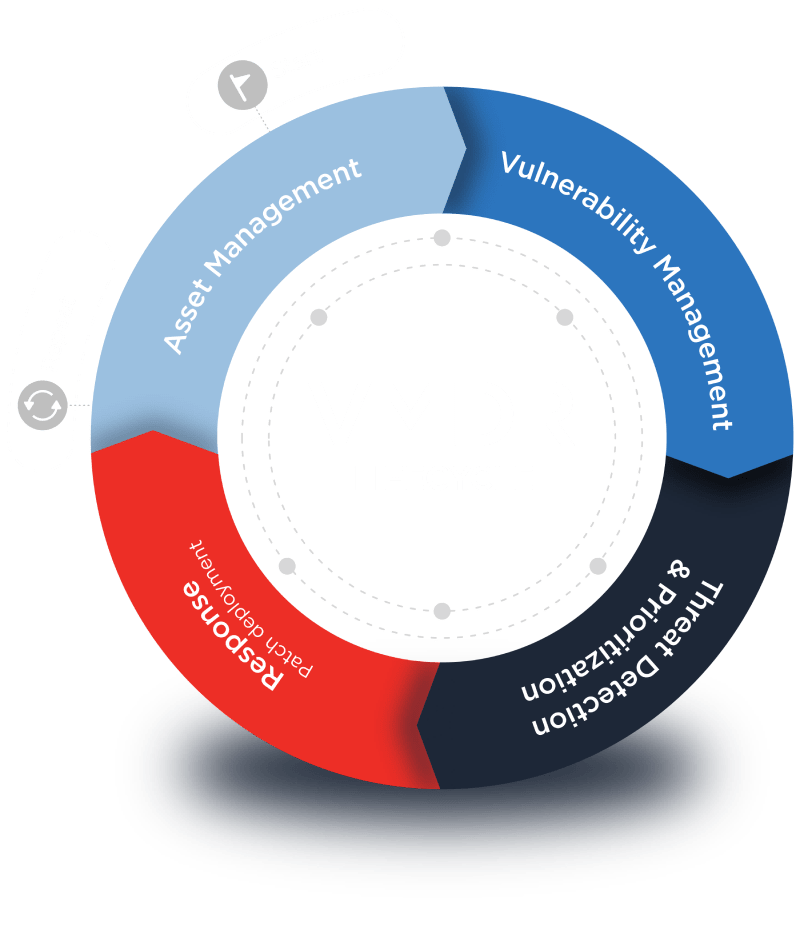
Vulnerability Management
Vulnerability management is the process of identifying, evaluating, treating, and reporting on security vulnerabilities in systems and the software that runs on them.
Application Security
Build secure software fast. Our application security platform automates testing throughout the CI/CD pipeline so developers can quickly resolve issues.Focus on what matters most with low false-positive rates.
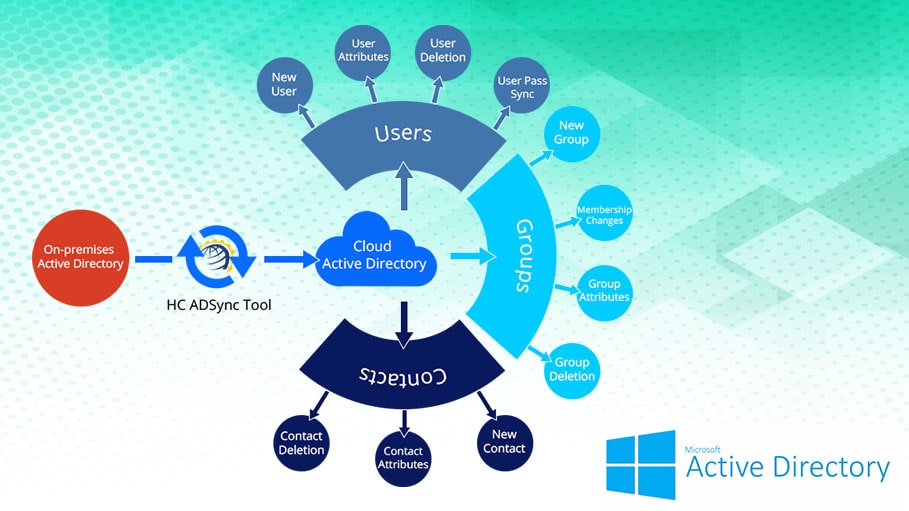
Active Directory Security Assessment
Active Directory (AD) protects the keys to the enterprise kingdom. There are only a handful of vital IT assets that attackers use to spread after initial infection, and AD remains the root of most compromises.
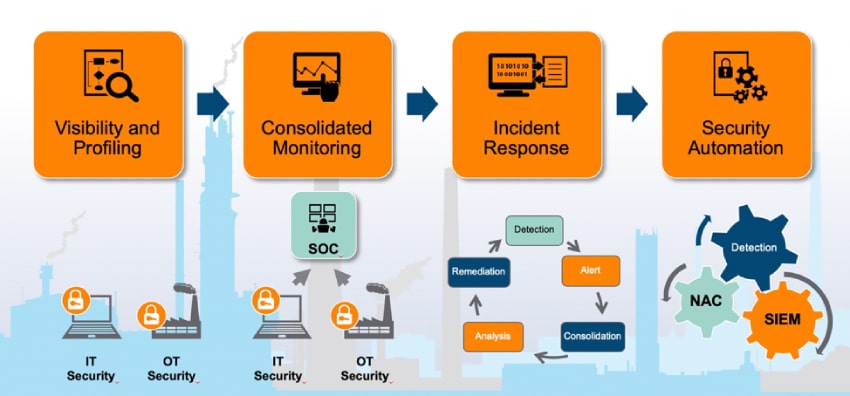
OT security
OT Security is the full stack of hardware and software being used to monitor, detect and control changes to devices, processes and events.
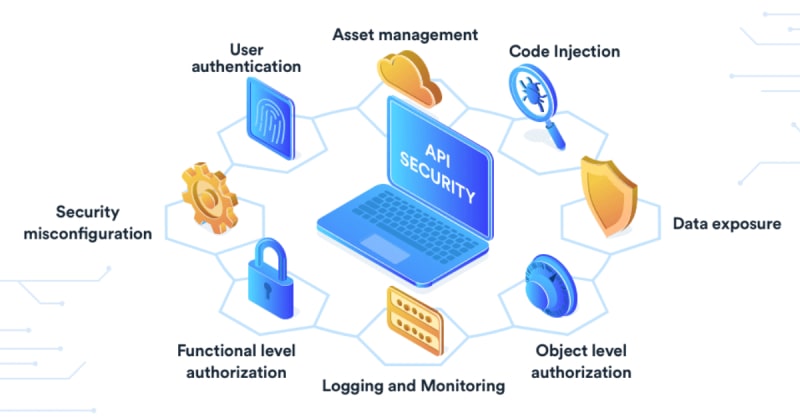
API security
Our solution delivers the context you need to protect your APIs across build, deploy, and runtime phases.
Active Directory Audit
Our solution for Active Directory delivers security intelligence about what’s going on in Active Directory and Group Policy.
Application White Listing
Application whitelisting is the practice of specifying an index of approved software applications or executable files that are permitted to be present and active on a computer system.
Hardening Automation
Hardening, when applied to computing, is the practice of reducing a system’s vulnerability by reducing its attack surface.
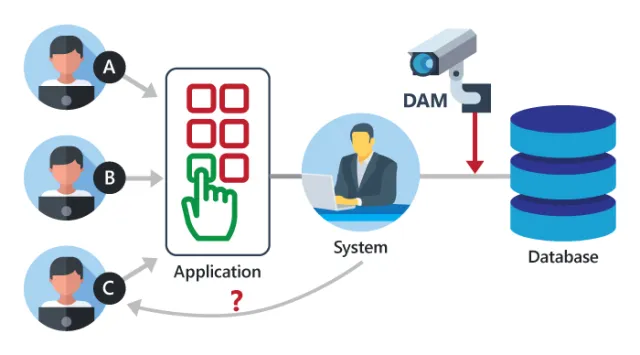
Database Activity Monitoring
Database activity monitoring is done by combining several techniques such as network sniffing, memory scraping and reading system tables and database audit logs. Regardless of the methods used, DAM tools enable data correlation so as to provide an accurate picture of all the activities in the database.Database activity monitoring (DAM) refers to a suite of tools that can be used to support the ability to identify and report on fraudulent, illegal or other undesirable behavior, with minimal impact on user operations and productivity.
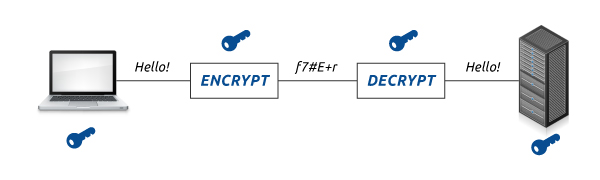
SSL Decryption
SSL Decryption, also referred to as SSL Visibility, is the process of decrypting traffic at scale and routing it to various inspection tools which identify threats inbound to applications, as well as outbound from users to the internet.Encryption and decryption are the heart of the SSL security algorithm in which information traverse between browser and server is converted into encrypted text
Malware Sandboxing
Keeping the organization safe from advanced threats sounds like a challenging task because it is. One of the key requirements is to quickly and efficiently detect malware, both known and unknown.
Security Awareness and Training
Over 90% of successful cyber attacks are down to human error. Threats like phishing, ransomware and other forms of social engineering continue to plague organisations of all sizes.It’s time to change user behaviour and reduce the cyber risk.Launch interactive security awareness and training programs to educate and empower your end users.
Email Security
Fast interception of any content-borne attack across all collaboration channels including email, cloud storage, CRM apps, and messaging platforms. We prevent phishing, BEC, spam, malware, Zero-days, and N-days well before they reach your end-users.Today’s enterprises can’t afford to be held back by slow,
Digital Supply Chain Monitoring
Our platform offers a novel and critical approach for enterprises to discover and control the new attack surface created by hyperconnected online ecosystems and predominantly unmonitored and unmanaged resources that are vulnerable targets.
Dark Web Monitoring
Our AI Platform helps enterprise customers to test,secure and protect their applications, cloud and infrastructure, reduce supply chain attacks,.
Cyber AI
Our AI solution interrupts in-progress cyber-attacks in seconds, including ransomware, email phishing, and threats to cloud environments and critical infrastructure.Attackers can strike when security teams are out of office and response times are slower.
External Security Posture Assessment
Our platform offers a novel and critical approach for enterprises to discover and control the new attack surface created by hyperconnected online ecosystems and predominantly unmonitored and unmanaged resources that are vulnerable targets..